Blog
What Small Businesses Need to Know About Cyber Security and Password Management
20/09/2021
What Small Businesses Need to Know About Cyber Security and Password Management
Small to medium businesses (SMBs) made tough choices this past year to keep their business running. Staff scattered to work from home—unexpectedly—and SMBs had to quickly enable them with tools and support to stay connected. Many small companies were forced to sacrifice cyber security best practices in favor of business productivity, increasing their risk of attack.
43% of cyber attacks are aimed at small businesses, but only 14% are prepared to defend themselves, according to Accenture’s Cost of Cybercrime Study.
For many SMBs, a cyber attack—especially one that results in stolen data and loss of customer trust—can spell the end. Data breaches often result in reputation damage, legal damages, and financial loss. The total cost of a single data breach for an SMB is approximately $150k. Unfortunately, many SMBs lack cyber insurance and savings that could help them absorb that cost.
If you’re a small business owner or leader, you need to know: What steps can small businesses take to reduce their cyber risk? How can small businesses prioritize cyber strategies to match limited budgets and resources? And, what requirements do small businesses need to consider when selecting cyber security tools?

SMB cyber risk mirrors enterprise in many ways
Cyber threats for organizations with under 1,000 employees are starting to mirror enterprises, according to the 2021 Verizon Data Breach Investigations Report. Among the latest findings:
Both SMBs and enterprises are facing the continued rise of social attacks, such as phishing—the #1 attack vector.
Both SMBs and enterprises are being targeted by financially motivated organized crime actors and are increasingly victims of ransomware. In fact, almost half (46%) of SMBs have been targeted by ransomware, and nearly 75% of victims have paid a ransom to gain back data and restore control of their systems.
Both SMBs and enterprises are moving to the cloud and using a variety of web-based applications – often chosen by individual staff or business functions vs. a central IT team—that may not follow security best practices for authentication and permissions.
Cyber issues of particular concern for SMB
While small businesses share the same risk as enterprises, they also have special concerns.
SMBs have fewer cyber security professionals and tools for protection. In our most recent research of global CISOs, we found that smaller organizations are least likely to have implemented protection such as multi-factor authentication (MFA) and virtual private networks (VPNs), and the least likely to have received training in the last year compared to larger organizations. These factors increase the risk of cyber attack.
Which cyber security tools are the best fit for SMBs?
SMBs often ask: Where do I find the cyber security tools that fit a limited budget and small team? Which investments should I make when I can’t afford everything an enterprise can?
SMBs are very good at prioritizing to survive. With a small budget and few if any dedicated security personnel, you need tools that give you the biggest bang for the buck.
The problem with adopting consumer-based password management tools
SMBs are more likely to consider using consumer-based tools for password management. These tools are designed for individual consumers to keep track of passwords and are typically siloed mobile applications people manage on their own.
Which password management tools are best for SMBs?
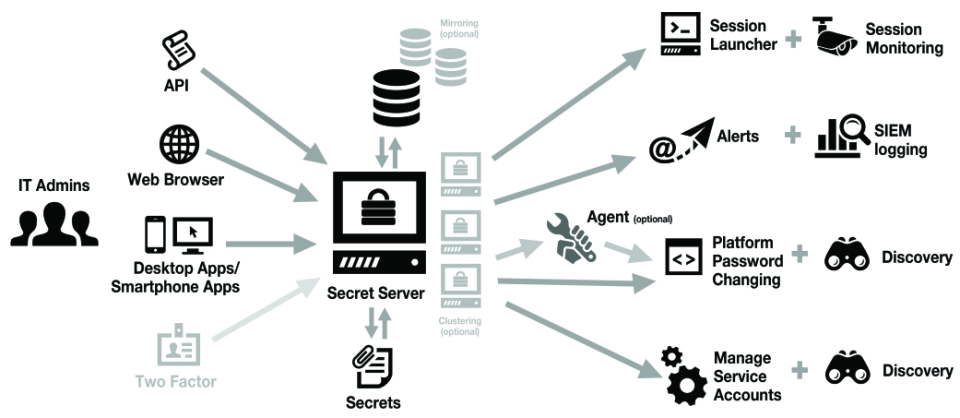
A unified approach with privileged access management (PAM) is more secure and efficient than disconnected personal password managers.
PAM solutions automatically create and rotate passwords, ensuring that when passwords are changed, all dependencies—systems that are connected to those passwords—can still authenticate and connect.
Organizations use PAM software to control who can use a privileged account or access sensitive information with the ability to adjust permissions and change or delete critical data. They treat the privileged account as the object that is being protected, restricting password disclosure and sharing, while providing time-limited access to critical systems. Once a password is no longer required it’s rotated or expired so employees or third parties can’t continue to access sensitive information with old passwords.
PAM solutions offer session recording capabilities to enable forensics and generate compliance reports that satisfy auditor requirements.