solution
Thycotic Protecting The Federal Government From Insider Threats
11/09/2021
Thycotic Protecting The Federal Government From Insider Threats
How Are You Protecting Government Data?
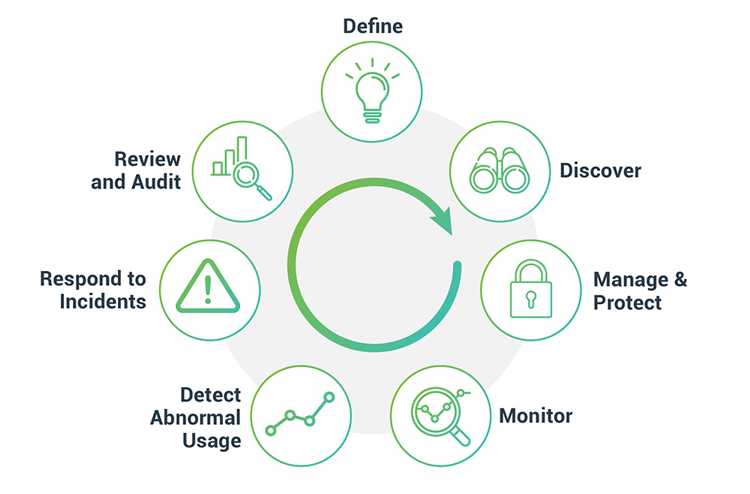
Thycotic’s privilege management gives Federal agencies and government contractors simple, automated controls to secure confidential information, and to meet the US Department of Homeland Security CDM requirements.
Challenge
Malicious threat agents and state-sponsored attacks are targeting Federal government IT systems.
Danger
Attacks can disrupt mission-critical operations, corrupt or steal classified information, and deny essential services.
Solution
- Privilege management secures access to data and systems to prevent and defend against cyber attacks.
- Privileged credentials must be managed and secured to protect billions of federal records
The most sensitive data and critical IT systems managed by the federal government are accessible to anyone with the right credentials. Privileged management solutions, including role-based access control, encryption, multi-factor authentication, and enforcement of a least privilege policy, are an essential part of a cyber security strategy for all federal agencies and contractors.




