solution
Privileged Access Management (PAM)
11/09/2021
Privileged Access Management (PAM)
Master the basics of privileged access management and discover the next steps you’ll take to start managing privileged accounts as an expert.
-
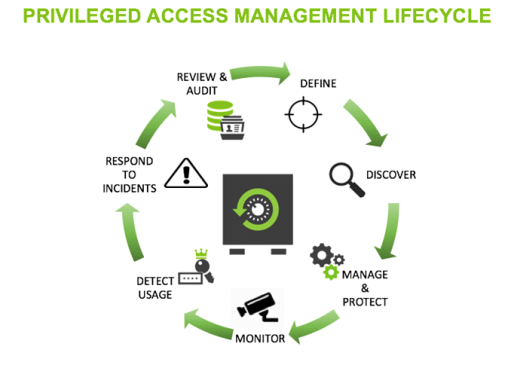
INTRODUCTION TO PRIVILEGED ACCESS MANAGEMENT
This overview builds your understanding of PAM so you can set the foundation for a comprehensive privileged access management strategy. We’ll cover:
- What an IT professional should know about how privileged accounts function and the risks associated with their compromise and misuse.
- How you can use this knowledge to make your organization much less vulnerable to potential monetary and reputational damage from increasing threats.
You’ll gain a practical understanding of privileged access management and its benefits to your organization. You’ll learn what privileged accounts are, where they’re located throughout an IT environment, and how they function. Most importantly, you’ll understand the risks associated with these accounts and learn how implementing a privileged account security solution can protect you from malicious insider and external threats.
-
KEY PRIVILEGED ACCESS MANAGEMENT DEFINITIONS
First, let’s define some key terms you need to know to understand PAM.
What’s the difference between privileged access management and privileged account management (both called PAM)?
The PAM industry began with the core capabilities of privileged account management. Privileged account management is the IT security process of using policy-based software and strategies to control who can access sensitive systems and information. Privileged accounts rely on credentials (passwords, keys and secrets) to control access. By creating, storing, and managing these credentials in a secure vault, privileged account management controls authorized access of a user, process, or computer to protected resources across an IT environment.
Since the early days of PAM, however, privileged security strategies have expanded and the common definition of PAM has changed. Today, most people define PAM as privileged access management. This definition of PAM reflects a broader security category than privileged account management. It includes cyber security strategies for exerting control over elevated access and permissions for users, accounts, and processes. It determines not only which people and systems can access a privileged account but also what they can do once logged in.
Additionally, this definition of PAM incorporates strategies which provide security teams with more granular control and oversight over the actions taken during privileged sessions. It includes managing the passwords of a privileged accounts through tactics like credential management, least privilege enforcement, and account governance. For example, privileged access approval and workflows, two-factor/multi-factor authentication, privileged session monitoring and recording, and remote launching are critical elements of a comprehensive privileged access management program.
What’s the difference between user accounts and privileged accounts?
There are two major categories of IT accounts:
- User Accounts: A user account typically represents a human identity (such as an Active Directory user account) and has an associated password to protect information and prevent anyone else accessing without permission. There is usually a single account password per user that needs to be memorized by a person.
- Privileged Accounts: Privileged accounts provide administrative or specialized levels of access to enterprise systems and sensitive data, based on higher levels of permissions. A privileged account can be associated with a human being or non-human IT system.
Organizations often have two to three times more privileged accounts than they have employees. In most organizations, IT staff have one account with standard-level permissions and another account for performing operations that require elevated permissions.
What are privileged accounts used for?
Privileged accounts are the keys to your IT kingdom because they can be used to access a sensitive server, adjust permissions, make backdoor accounts, or change or delete critical data.
Privileged accounts that need elevated permissions include:
- Local or Domain Admin accounts that manage servers
- Domain Admin accounts that typically control Active Directory users
- SA accounts, or system admin accounts, that help manage databases
- Root accounts that manage Unix/Linux platforms
- Accounts that run and manage Windows applications, services, and scheduled tasks
- IIS application pools (.NET applications)
- Networking equipment accounts that give access to firewalls, routers, and switches
What are privileged service accounts?
A service account is a special category of privileged account that requires elevated privileges to run scheduled tasks, batch jobs, application pools within IIS, and more across a complex network of databases, applications, and file systems. Hundreds or thousands of services rely on privileged accounts to run critical IT processes. As such, service accounts are among the highest risk privileged accounts.
Unfortunately, service accounts are also typically the most misused types of privileged accounts. To keep systems running and avoid downtime, they’re often configured with unnecessarily high levels of privilege. Without human owners, they often lack oversight. As a result, service account passwords aren’t rotated, expiration dates pass or are never set, and accounts are never decommissioned. These common practices create a dangerous vulnerability for any organization, opening the door to cyber attacks.
Who uses privileged accounts and where are privileged accounts located?
The typical user of a privileged account is a system administrator (sysadmin) responsible for managing an environment, or an IT administrator of specific software or hardware. They need elevated privileges to:
- Install system hardware/software
- Access sensitive data
- Reset passwords for others
- Log into all machines in an environment
- Make changes in IT infrastructure systems
Privileged accounts are used by systems administrators to deploy and maintain IT systems, so they exist in nearly every connected device, server, database, and application. Privileged accounts extend well beyond an organization’s on-premise or cloud-based enterprise infrastructure to include employee-managed marketing, sales, financial, and social media accounts. Therefore, it’s important that even small and medium businesses have an efficient privileged account management process in place.
What’s the difference between identity and access management (IAM) and privileged access management?
The domain of privileged access management is generally accepted as part of the broader scope of identity and access management (IAM). However, identity and privilege are inextricably linked and, as tools and solutions become more sophisticated, the lines continue to blur.
Identity refers to people. You, your boss, the IT admin, and the HR person are only a handful of examples of people who may be responsible for creating, updating, or even deleting attributes. The core objective of IAM is having one digital identity per individual. Once that digital identity has been established, it must be maintained, modified, and monitored.
Privileged access management is part of IAM, helping manage entitlements, not only of individual users but also shared accounts such as super users, administrative, and service accounts. A PAM tool, unlike IAM tools or password managers, protects and manages all types of privileged accounts. A mature privileged access management solution goes even further than simple password generation and access control to individual systems. It also provides a unified, robust, and—importantly—a transparent platform that is integrated into an organization’s overall identity and access management (IAM) strategy.
-
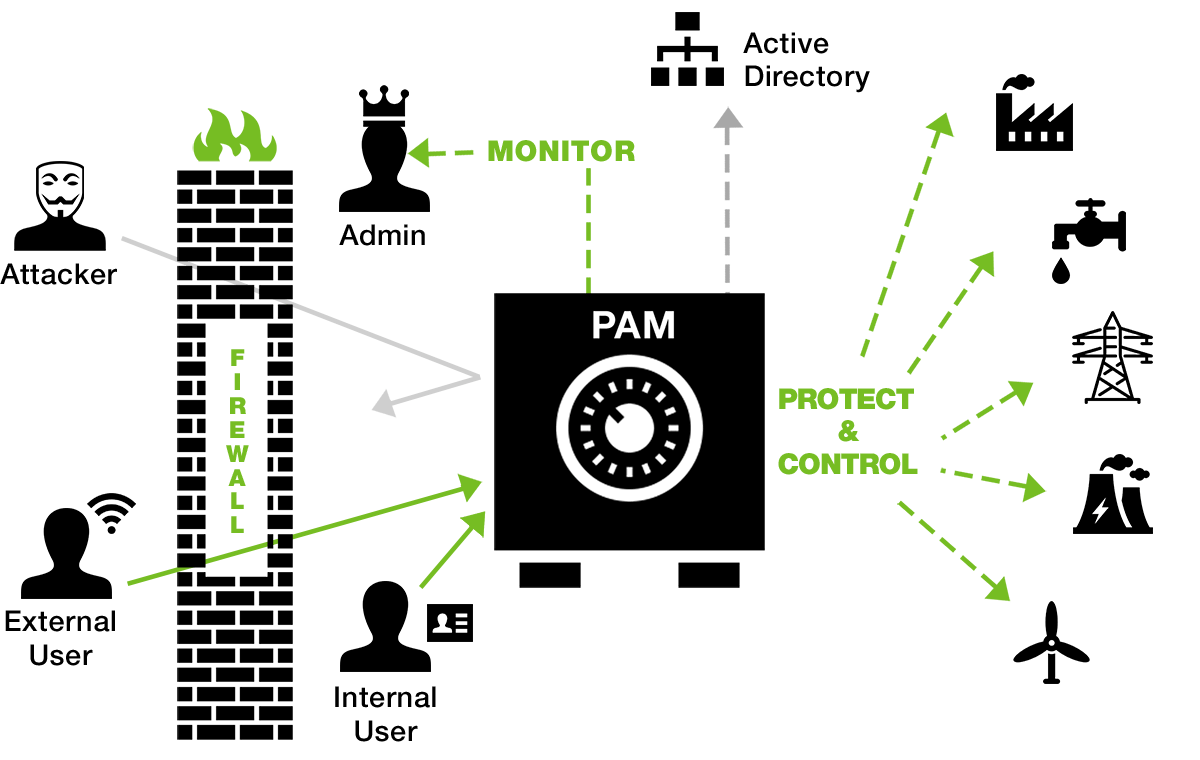
RISKS & VULNERABILITIES RELATED TO PRIVILEGED ACCOUNTS
What are the risks associated with unmanaged privileged accounts?
Many high-profile breaches have one thing in common: They were accomplished through the compromise of privileged credentials. Industry analysts estimate that up to 80% of all security breaches involve the compromise of privileged accounts.
Despite the risk, traditional methods of identifying and managing privileged accounts still rely on manual, time-consuming tasks performed on an infrequent or ad-hoc basis. Even in the most sophisticated IT environments, privileged accounts are all too often managed by using common passwords across multiple systems, unauthorized sharing of credentials, and default passwords that are never changed—making them prime targets for attack.
These practices can easily compromise security because for most attackers taking over low-level user accounts is only a first step. Their real goal is to take over privileged accounts so they can escalate their access to applications, data, and key administrative functions. For example, in many cases, local domain accounts on end-user devices are initially hacked through various social engineering techniques. Attacks are then escalated to gain access to more systems.
Virtually all organizations have some unknown or unmanaged privileged accounts, increasing their risk. Some have thousands. This can happen for various reasons:
- An ex-employee’s access was never disabled.
- An account is utilized less and less often until it becomes obsolete and is abandoned.
- Default accounts for new devices were never disabled.
Every unknown or unmanaged privileged account increases your organization’s vulnerability and presents an opportunity for an intrusion. An employee may access it to perform unauthorized tasks, intentionally or unintentionally, breaking compliance regulations, and increasing your liability. A disgruntled ex-employee who retains privileged access can cause harm.
A cyber criminal can find the account and penetrate your organization, steal information, and wreak untold havoc.
If a single privileged account is used across your organization to run many services or applications, when that account is breached, your risk increases exponentially. In that case, it only takes one compromised privileged account for an attacker to gain access to virtually any information within your organization’s IT network.
How does the cloud increase your risk of a privileged account attack?
As businesses migrate to the cloud, the diversity of privileged access management use cases expands. In a cloud model, managing privileged access to workloads, services, and applications remains your responsibility, not the cloud providers’. It’s also your responsibility to make sure data going to and from the cloud (via Web browsers, Email, File exchanges such as SFTP, APIs, SaaS products, and streaming protocols) is properly secured.
Unfortunately, many organizations aren’t adequately implementing and enforcing policies to control privileged access. The challenge exists not in the security of the cloud itself, but in the policies and technologies that control access, identities, and privileges. In nearly all cases, it’s the user, not the cloud provider, who fails to manage the controls. According to Gartner, through 2023, at least 99% of cloud security failures will be the customer’s fault, with 50% of issues attributed to inadequate access, identity, and privileged management.
How do cyber-criminals compromise privileged accounts?
We’ve discussed the importance of privileged accounts, the central role privileged accounts play in managing systems, infrastructure and applications, and the risks associated with losing control of privileged accounts. Next, it’s important to understand the tricks and techniques cybercriminals use to wrest control of these accounts. In the next section, we’ll discuss what can be done to protect privileged accounts.
The path to compromising a privileged account often follows a variation of this pattern:
- Compromise a local account. Criminal hackers use malware or social engineering to get access to desktops, laptops, or servers. Employees are fooled by phishing scams that appear to be legitimate requests from an employee’s manager, company executive, or another trusted source. They may unknowingly click on a malicious link, download a piece of software with malware hidden inside, or enter their password credentials into fake websites.
- Capture a privileged account. An attacker’s primary goal is to obtain a privileged account (such as a local Windows administrator account) to move around. After an employee’s password is captured, the perpetrator can log onto a network and simply bypass many of the traditional IT security controls because they appear as a user with legitimate credentials. Common techniques include Man in the Middle or Pass the Hash attacks to elevate privileges.
- Hide and observe. Sophisticated criminal hackers are patient, preferring to remain undetected rather than crack-and-dash. After attackers establish a breach, they typically use compromised privileged accounts to perform reconnaissance and learn about the normal routines of IT teams. This includes observing regular schedules, security measures in place, and network traffic flow. They use these observations to blend in and make sure they don’t trigger any network security alarms. Eventually they can get an accurate picture of the entire network and its operations.
- Impersonate employees. An attacker with access to a privileged account can impersonate a trusted employee or system and therefore can carry out malicious activity without being detected as an intruder. When attackers compromise a privileged account, they can operate undetected for weeks or months at a time. Because a compromised privileged account appears to be a legitimate user, it’s very difficult to find the root cause or perform digital forensics when a breach is eventually detected.
- Establish ongoing access. An attacker’s next step is often to establish ongoing access by installing remote access tools, which enables them to return anytime they wish and perform malicious activities without raising an alarm.
- Cause harm. Depending on the motive of the attackers, they can use privileged accounts to do things such as:
– Damage system functions or disable access by an IT administrator
– Steal sensitive data for fraud or reputation damage
– Inject bad code
– Poison data
-
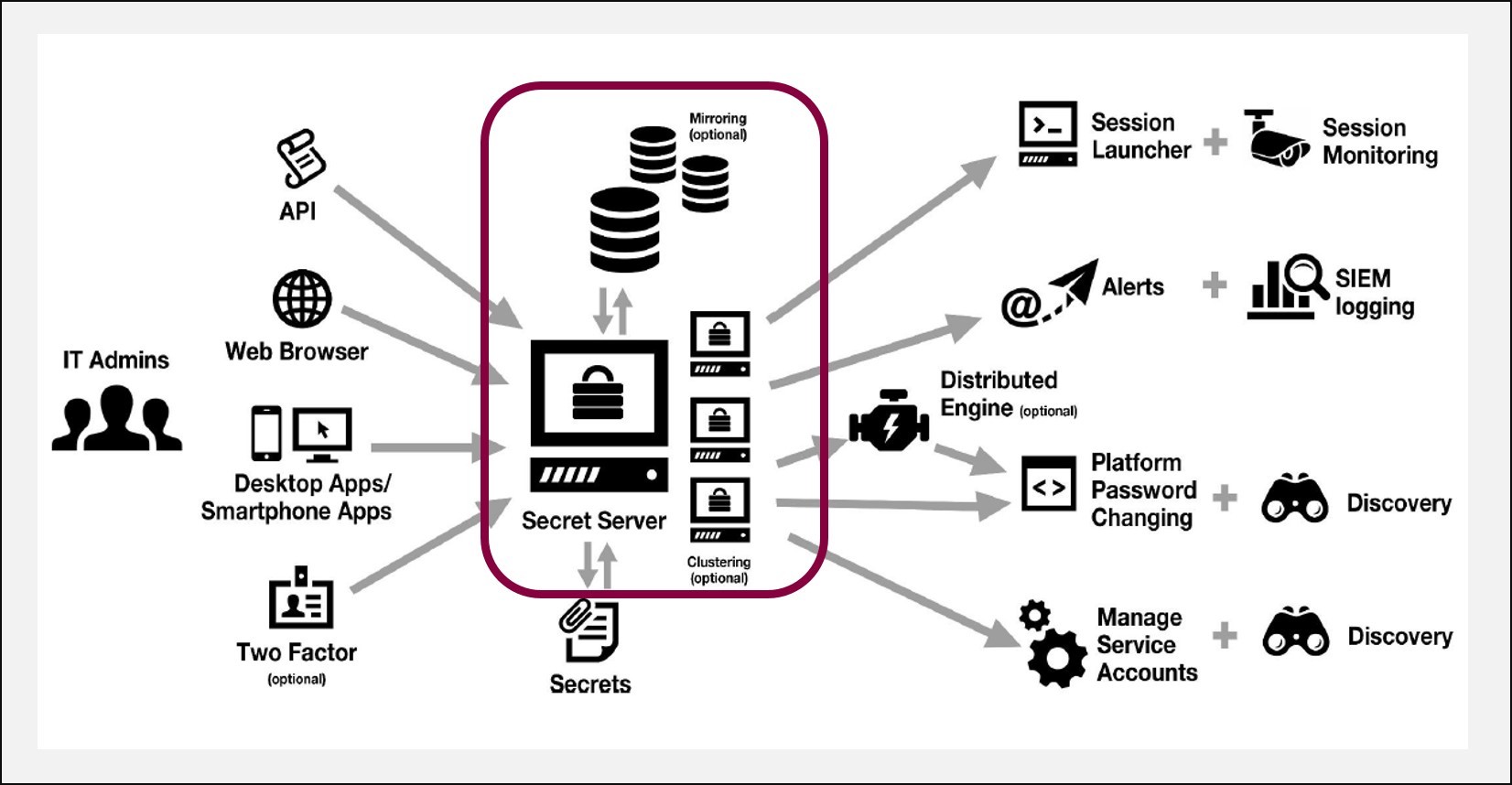
PREVENTING PRIVILEGED ACCOUNT ATTACKS WITH PAM
How does PAM lower your risk of a privileged account attack?
The overall goal when designing your privileged access management process and implementing solutions is to arm IT and security professionals with tools they need to control access within their corporate environment, thus reducing the attack surface by limiting privileged access and behavior. Ultimately, by implementing a PAM solution in conjunction with other IT security best practices, you can contain potential damage related to attacks originating external to your organization, or those instigated internally, regardless of whether an action is due to intentional maliciousness or inadvertent incompetence.
-
HOW TO DEVELOP A COMPREHENSIVE PAM SOLUTION
Critical questions to answer when getting started
Like any IT security measure designed to help protect critical information assets, proper privileged access management requires both an initial plan and an ongoing program. You must identify which privileged accounts should be a priority in your organization, as well as ensure the people who are responsible for managing your privileged accounts are clear on their acceptable use and responsibilities.
Before you can successfully implement a privileged access management solution, a planning phase must answer several key questions:
How do you define a privileged account for your organization?
Map out what important functions rely on data, systems, and access. Identify important systems which would need to be recovered first in the event of a breach. Then you can identify the privileged accounts for those systems. Classifying privileged accounts at this stage is good practice because this helps prioritize privileged accounts and will make decisions easier when it comes to applying security controls.
Who needs access to your privileged accounts?
Privileged accounts should be categorized as: a) human, b) applications and services, c) systems, and d) infrastructure accounts, including cloud-based accounts. These classifications will determine the level of interaction and security controls which should be applied to each privileged account. For applications and systems, ask yourself how often rotating the passwords is required and if the path to the system is static so you can restrict IP addresses that can use the privileged accounts.
Do you rely on third-party contractors that need access?
Third-party contractors that need access to privileged accounts can be one of the highest risks because you don’t have full control over how they access and manage privileged accounts. Make sure you include these use cases in your planning and identify how those accounts should be created, governed and eliminated as contracts are completed.
Do you set time windows for privileged account usage?
Knowing when specific privileged accounts are supposed to be used indicates normal behaviors that allow you to identify possible abuse or misuse. Accounting systems, for example, may only require access at the end of the month or quarter. Backup systems typically run at scheduled times. Integrity validation and vulnerability scanning probably will follow a scheduled penetration test.
What happens if privileged accounts are compromised?
Many organizations aren’t prepared when an account is breached and typically default to simply changing privileged account passwords or disabling the privileged account. That’s not enough. A comprehensive incident response toolkit helps you prevent a cyber attack from turning into a cyber catastrophe by ensuring key areas are addressed, such as:
- Steps to take before an incident occurs to make sure people are prepared to act
- Indicators of compromise that help you discover a privileged attack
- Actions to take during each phase of an incident to contain the damage
- Strategies that help you continue normal business operations even while under attack
What’s the risk of privileged accounts being exposed or abused by an insider? Protecting privileged accounts from insider misuse or abuse should focus on your most critical systems. Most employees, for example, shouldn’t be given access to all critical systems at the same time, including production systems, backup systems, and financial systems. Employees changing jobs within your organization shouldn’t be able to keep the same access from their previous roles.
Do you have an IT security policy that explicitly covers privileged access management?
While a lot of companies have a corporate IT policy in place, many still lack acceptable use and responsibilities of privileged accounts. Create a privileged account password policy that treats privileged accounts separately by clearly defining a privileged account and detailing acceptable use policies. Be sure to include who’s responsible and accountable for using privileged accounts.
Do you have to comply with government or industry regulations?
If your company must comply with certain industry regulations, it’s critical to get privileged accounts secured. Many organizations must undergo regular internal and external audits to comply with policies and legal requirements. That means demonstrating to auditors that your privileged accounts are audited, secured, and controlled.
What reports does your CISO expect on privileged account use and exposure?
Discuss with your CISO your goals for a PAM program and how you’ll measure success. If you can’t properly observe what’s going on with your privileged accounts, you increase your risk. If a breach does occur, monitoring privileged account use helps digital forensics identify the root cause and identify critical controls that can reduce your risk of cyber security threats.




