Security Manager
Security Manager – FireMon
The enterprise network is a complex machine. New network segments, new hosts and zero-day vulnerabilities are just a few of the moving parts that make securing access a formidable task. And while you’re trying to secure a network that’s constantly in transition, requirements to prove continual compliance with industry regulations and best practices further complicate your security management challenge.
Firewalls are only as effective as the rules that control access into and out of your enterprise — rules that can only be effective if they are managed well. Firewall management requires more than just allowing or denying access to destinations and ports however.
Do you know:
- Why the business needs each firewall rule?
- Which rules pose the most risk?
- Which rules should be removed next month?
- How many rules you have and how many more are on the way?
- Which new rules are actually redundant?
To manage your firewall well, you need to decide if a rule goes in or is pulled out and justify that decision with data before it is implemented. You want to capture the business justification in the change process and keep it where you can use it. You must keep the rules clean and run compliance checks every time the firewall configuration changes.
What is Security Manager?
 FireMon’s Security Manager finds the holes in your network security infrastructure before the bad guys do. A proactive, real-time security management solution, Security Manager detects your network weaknesses and makes recommendations for reducing susceptibility to threats. It can improve security
FireMon’s Security Manager finds the holes in your network security infrastructure before the bad guys do. A proactive, real-time security management solution, Security Manager detects your network weaknesses and makes recommendations for reducing susceptibility to threats. It can improve security
by showing you a forgotten host in the DMZ that can access the internal network, a dormant security rule that provides unnecessary access, or how a multi-exploit attack could pivot deep into the network.
Built for the Enterprise, Security Manager provides the solution to this challenge by analyzing your network’s posture. It monitors a consistent stream of configuration and event data from firewalls, routers, switches and load balancers, and collects host vulnerability data from network scanners to provide a complete picture of the strengths and weakness of your network.
With that data securely collected in a role-based, multi-tenant data store, Security Manager’s patented analysis engines apply a deep knowledge of the behavior of your network to help you find, visualize, overcome and ultimately avoid potential problems. Measure the risk from threats in seconds, understand the network
configurations that make them accessible, avoid impacting business continuity while ensuring secure access, find and clean up legacy infrastructure elements, and automatically report on your posture and compliance. With Security Manager you can proactively fix your legacy challenges and be prepared to meet the security demands of tomorrow.
Manage and control change continuously
Configuration changes happen constantly and to control them you need a change management system that gives you immediate access to change justification and clear communication channels. FireMon’s Security Manager gives you six powerful tools for firewall change management.
IMMEDIATE CHANGE NOTIFICATION
Team members can make changes at any time of the day or night. Security Manager monitors your firewall continuously to capture all changes, planned or not, malicious or innocent, and alerts the right people. Notifications can be sent to team members in easy-to-read emails, or to monitoring systems via syslog.

FIREWALL-SPECIFIC CHANGE REQUESTS
You can improve change effectiveness by getting better information from your users. Learn more about what access they need—and why they need it—with a firewall-specific change request form.
CHANGE CONTROL TRACKING
Track the change control number alongside the technical implementation details of the change. Use Security Manager reports to quickly find changes that lack proper documentation.
CHANGE CONTROL REPORTS
Search and report instantly on implementation details for any change control number. The report includes who implemented the change, when it was implemented, and on which firewall(s).
GRAPHICAL CHANGE REPORTS
Know immediately what changes have occurred and see what has changed with one glance.
AUDIT LOGS
Track who changed what in the firewall using an easy-to-use, line-by-line format.
Clean up your Firewalls
Policies expand and grow complex as thousands of rules and objects are added. Keeping up with these changes and additions is a daunting process, but without it, firewalls grow less efficient and change implementation gets riskier. Security Manager automates the change process, running time-consuming, repeatable tasks for you so you can get more done faster and with less effort.
DAILY ACTIVITY REPORT
Security Manager collects a lot of data every day and you need to stay on top of it. The Daily Activity Report gets you started whether you need to know if the firewalls had a busy day or you’re troubleshooting why response seems slow.
FIREWALL COMPLEXITY REPORT
With Security Manager it’s easy to identify which firewalls need cleanup because their rule base has become overly complex. A single view across all firewalls quickly shows if access is too broadly defined and which specific rules are the primary cause.
Firewall complexity affects not only performance, but also operational management. The less complex you can make the rule set, the faster traffic will be evaluated by the system and the easier it will be for network engineers to manage access on a day-to-day basis.
HIDDEN RULES REPORT
Rule sets are large and complex. But knowing when the policy contains conflicts is a great way to stay on top of the rules that need to be cleaned up. Security Manager’s Hidden Rules Report analyzes your rules and provides specific, concrete recommendations.
RULE USAGE ANALYSIS
Once access has been requested and granted, removing it can be difficult. You can tackle this problem pro-actively by monitoring which rules are being used and removing the unused ones when needed.
OBJECT USAGE ANALYSIS
Even when a rule is used, Security Manager’s analysis engine drills down and determines which objects in that rule are unused. This empowers you to further clean up the rule and limit unnecessary access.

Comply with Regulations and Standards
TRAFFIC FLOW ANALYSIS
Auditors often find rules that are too broad for their purpose—and you must fix them after the fact. Security Manager’s Traffic Flow Analysis keeps you on top of things by watching the traffic on a single rule and showing how you can more narrowly define it. Use Traffic Flow Analysis to remove all unnecessary “Any” objects from your accept rules.
PCI ASSESSMENT
Security Manager’s knowledge of the rule base can help you comply with PCI- DSS Requirement. Because it knows the zones that affect PCI-DSS requirements, it can find and report on any failures.
CUSTOM COMPLIANCE REPORTING
Compliance is different for each organization and industry. Security Manager supports extensions for unique compliance requirements. FireMon encourages you to participate in our Nexus firewall management community and share your best practices for addressing compliance and other challenges.

Expand Visibility of Enterprise Network Behavior
Firemon ACCESS PATH ANALYSIS – REMEDIATE RISK WITHOUT HAVING TO PATCH

When risk exists in the network (i.e. a path from a threat to a vulnerability) there used to be only one alternative — patch.
With FireMon Access Path Analysis you have options. Access Path Analysis identifies the detailed risk path through the network, including the interfaces, routes, security rules and address translation rules that allow the access path that introduces risk.
It gives network security operators the information necessary to make a precise change and reduce risk without impacting network operations.
FireMon INSIGHT – CONFIGURATION INTELLIGENCE FOR NETWORK SECURITY
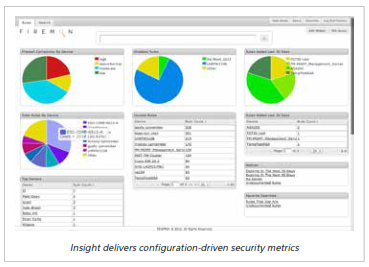
The configurations of your network security devices are the critical definitions that keep the wrong people out and let the right people in. But with thousands of devices working in concert – all with proprietary configurations and overly complex rule sets – it can be difficult to make sense of it all. That’s where FireMon Insight fits in. This real-time dashboard gives each user a one-stop view of the critical metrics from across your security configurations , including the configurations of all major firewall vendors.
Assemble a dashboard from pre-built widgets to see things like the most complex devices across your organization, most recent changes, top unused rules, or rules with excessive access. Build ad-hoc queries using FireMon’s domain-specific query language and export the results as a PDF or CSV file. Save your custom queries as a Favorite on your dashboard for quick future access.
FireMon also exposes the same Insight platform capabilities via RESTful Services, allowing you to build complex network analyses and configuration-based security metrics into other line-of-business applications, reports, and portals.
We’re Ready To Help You
Get in touch with us today and let’s start transforming your business from the ground up.