DDOS ATTACK PREVENTION SOLUTION FROM NETSCOUT ARBOR
I. CURRENT DDOS ATTACK SITUATION
- Attack Trends
Reports from Netscout covering the second half of 2023 to the present indicate several notable global DDoS attack trends:
- Increase in DDoS attacks from hacktivist groups: Groups such as NoName057(16) and Anonymous Sudan are using DDoS attacks to advance their political agendas. These groups demonstrate a high level of technical sophistication and cause significant damage to their targets.
- Attacks on DNS servers: Attacks targeting DNS servers are on the rise, causing widespread damage due to the dependency of numerous websites on these servers.
- Attacks on the gaming industry: The gaming industry is facing a growing wave of DDoS attacks, often aimed at disruption and extortion.
- Exploitation of IPv6 vulnerabilities: Attackers are exploiting vulnerabilities in IPv6, highlighting the need for specific IPv6 protection strategies.
- Use of DDoS botnets: Botnets remain a popular tool for DDoS attacks, enabling attackers to increase the scale and power of their assaults.
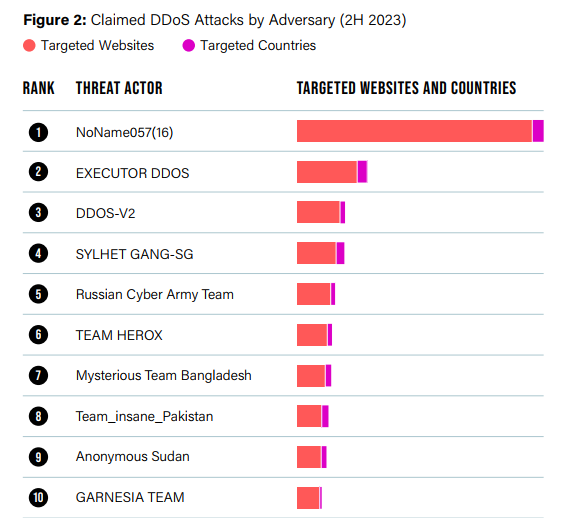
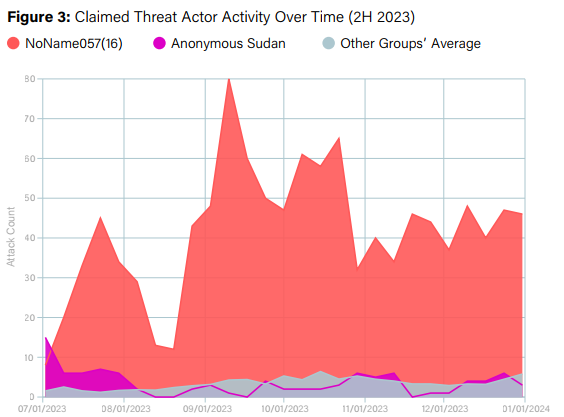
Industries frequently targeted by DDoS botnets include:
- Banking and Finance: Financial institutions are common targets for DDoS attacks intended to disrupt online services and steal sensitive information.
- Critical Infrastructure: Essential infrastructure like power grids, transportation systems, and healthcare databases are also vulnerable to DDoS attacks.
- Government and Military: Government and military agencies can be targeted to disrupt critical operations and steal classified information.
- Gaming and Entertainment: These companies are targeted to interrupt online services and impact revenue.
- Online Services: Social networks, e-commerce sites, and email services are attacked to disrupt operations and cause financial loss.
- Statistical Figures
According to a report from Netscout Arbor on DDoS attacks in Vietnam for the first six months of 2024 :
- Maximum Bandwidth: 720.4 Gbps
- Maximum Throughput: 69.43 Mpps (million packets per second)
- Average Duration: 60.43 minutes
- Total Peak Throughput: 132 Mpps
- Date of Peak Attack: March 5, 2024
Global statistics show that 53% of DDoS attacks last between 5 and 30 minutes. In the APAC region, the most common attack vectors in 2023 included TCP ACK, TCP SYN, and TCP RST floods. The most targeted industries in APAC were Wired Telecommunications Carriers and Data Processing/Hosting services.
II. TECHNOLOGY EVALUATION AND SELECTION
- Analysis of DDoS Attack Technology
A Denial-of-Service attack is a type of assault aimed at preventing legitimate users from accessing a service. These attacks can target any network device, including routers, web servers, email systems, and DNS servers.
There are five basic types of attacks:
- Consumption of computing resources like bandwidth, disk space, or CPU time.
- Disruption of configuration information, such as routing tables.
- Disruption of state information, such as the forced reset of TCP sessions.
- Disruption of physical network components.
- Obstructing communication between users and a victim to disrupt service continuity.
Attack Methods and Defense Strategies:
- Layer 3/4 Attacks: These include TCP ACK, TCP NULL, or TCP floods with random packets or headers. A defense system must be able to handle millions of concurrent connections and analyze each one to block malicious traffic before it reaches application servers . For SYN floods, the key defense is controlling the number of SYN/ACK requests in the TCP three-way handshake .
- Bandwidth Saturation Attacks: These attacks are often detected by significant changes in network traffic composition (e.g., a sudden spike in UDP or ICMP traffic) . Defense requires monitoring tools, bandwidth thresholding, and the ability to detect and block requests from botnets that mimic legitimate user traffic.
- Connection Exhaustion Attacks: Servers and stateful firewalls can only handle a finite number of concurrent connections . Attackers exploit this by creating a large number of spoofed, fake connections. To prevent this, a defense system must analyze and counter spoofing techniques (IP, browser, request) and limit the connection rate from a single source.
The most effective defense is to stop attacks at the source, but this is difficult due to the globally distributed nature of DDoS attacks . A comprehensive solution must combine global threat intelligence from network operators with on-premises tools for the most thorough protection.
- Technology Selection Evaluation
Many network devices like Firewalls, IPS, Load Balancers, and WAFs claim to have DDoS protection capabilities. However, their performance, scalability, and ability to quickly update defenses against new attack methods and botnets are often limited. Therefore, a dedicated DDoS prevention device is necessary.
Based on technology analysis and market evaluations from firms like IDC and Infonetics, Arbor Networks is the leading provider with over 50% market share and the most effective technology . Arbor offers a comprehensive solution portfolio, from on-premises appliances for individual customers to solutions for service providers and a cloud-based service, providing flexible deployment and the ability to handle massive attacks.
- Introduction to NETSCOUT Arbor
Arbor Networks, an American technology company founded in 2000, specializes in network monitoring products, particularly for the telecommunications sector. It is recognized as the pioneer in developing DDoS protection products for ISPs and IXPs. Today, Arbor’s solutions are deployed in over 90% of Tier 1 ISPs globally.
The ATLAS intelligence platform, a collaboration with over 400 ISPs, monitors more than 140 Tbps of global internet traffic, providing unparalleled visibility into threats.
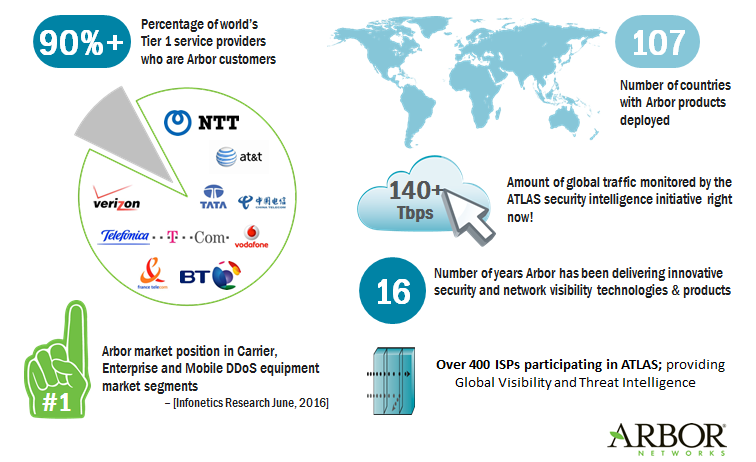
Key statistics:
- 90%+ of the world’s Tier 1 service providers are Arbor customers.
- Products are deployed in
107 countries.
- The ATLAS platform monitors
140+ Tbps of global traffic .
III. ARBOR’S IN-LINE DDOS PREVENTION SOLUTION
Arbor Networks offers the most comprehensive DDoS protection service, from small enterprise appliances to carrier-grade equipment and its own cloud service. A key feature is the ability for on-premises devices to integrate with ISP or Arbor cloud services via “Cloud Signaling” to mitigate volumetric attacks that saturate the internet link. Arbor’s cloud has a mitigation capacity of up to 11 Tbps.
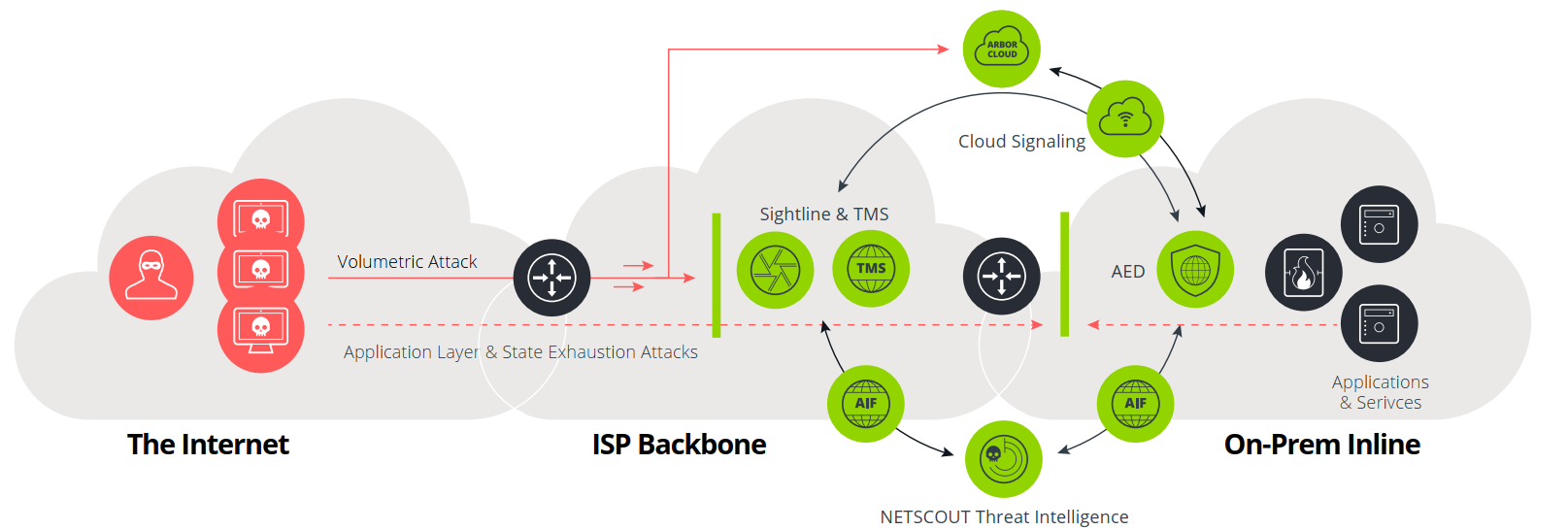 General Model and Operating Mechanism of Arbor AED
General Model and Operating Mechanism of Arbor AED
The core of the system is the Arbor Edge Defense (AED) device, which is deployed inline.
The AED is placed inline between two network segments, such as between ISP connections and the data center, to act as a first line of defense. The AED is a stateless device designed to protect stateful devices (like firewalls or routers performing NAT) from being overwhelmed by DDoS attacks. Placing the AED in front of internet routers ensures that these critical devices, as well as firewalls, IPS, and load balancers, are protected.

Operating Mechanism:
- The AED has two types of ports:
protection ports for handling traffic and management ports for configuration.
- Protection ports are arranged in pairs (e.g., “ext0” and “int0”). The “ext” port connects towards the external internet (the attack source), and the “int” port connects towards the internal protected systems.
- All inbound traffic passes through the “ext” port, where the AED analyzes it, blocks attack traffic, and forwards the legitimate, “clean” traffic out of the corresponding “int” port .
- Components of the Solution
The primary components of the inline DDoS solution are:
- DDoS Appliance Hardware: The main device that processes and blocks attack traffic.
- NIC Cards: These cards receive traffic and support various speeds (1G/10G/40G) with bypass functionality . Options include copper and fiber interfaces (SR, SX) .
- Licenses: The solution includes two main types of licenses:
- Clean Traffic License: A perpetual license, included with the hardware, that determines the maximum throughput of legitimate traffic the device can forward.
- AIF (ATLAS Intelligence Feed) License: A subscription-based license, renewed annually, that provides updates with the latest global DDoS threat intelligence.
- Features of the Arbor AED Solution
The Arbor AED is designed for enterprise deployment, offering simple management and powerful protection against application-layer attacks. It provides a comprehensive, on-premises defense that can be combined with cloud-based services for a hybrid approach.
The AED provides proactive monitoring and blocking for the following attack types:
- Application-layer attacks
- State-exhaustion attacks
- Volumetric attacks
- Inbound malware and other threats, utilizing a security database of over 3 million malicious IPs/DNS/URLs.
A key advantage of the AED is its
stateless technology. Unlike firewalls or IPS devices, it does not maintain a state table for all connections, making it immune to state-exhaustion attacks. It only tracks connections when necessary, ensuring high performance.
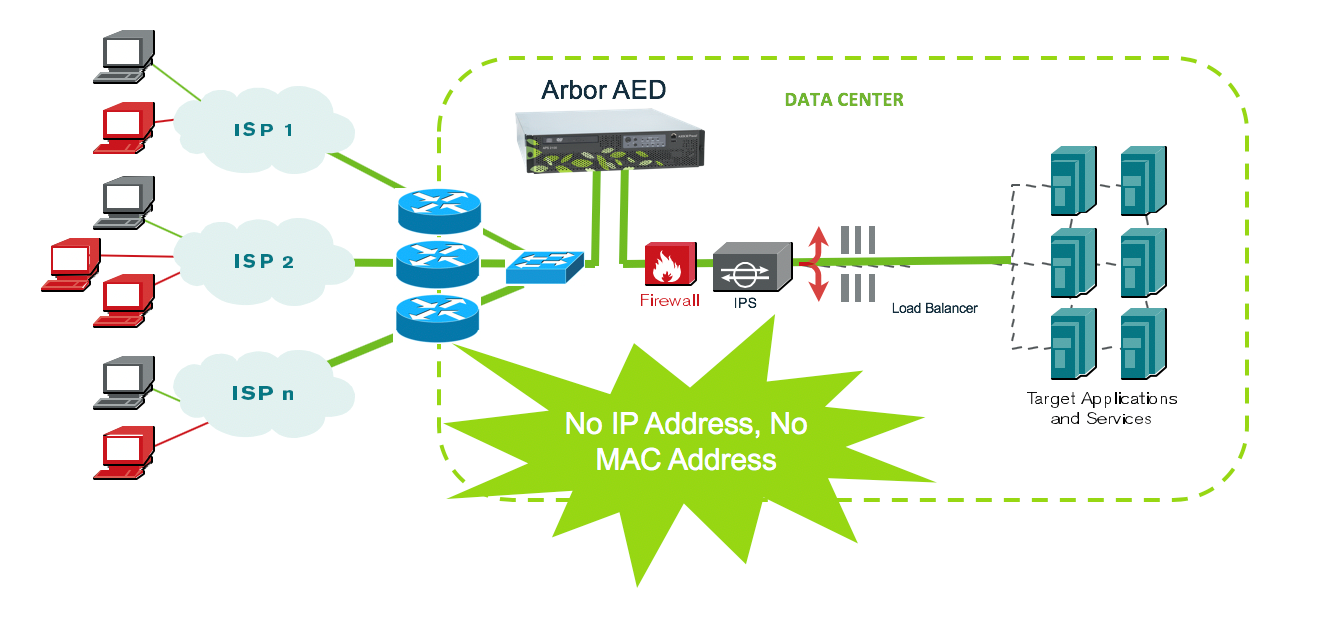
With the AIF (ATLAS Intelligence Feed) subscription, the device automatically receives updates from Arbor’s ASERT team, ensuring rapid response to new and emerging global threats. The AED also supports the STIX/TAXII standards, allowing integration with third-party threat intelligence databases.
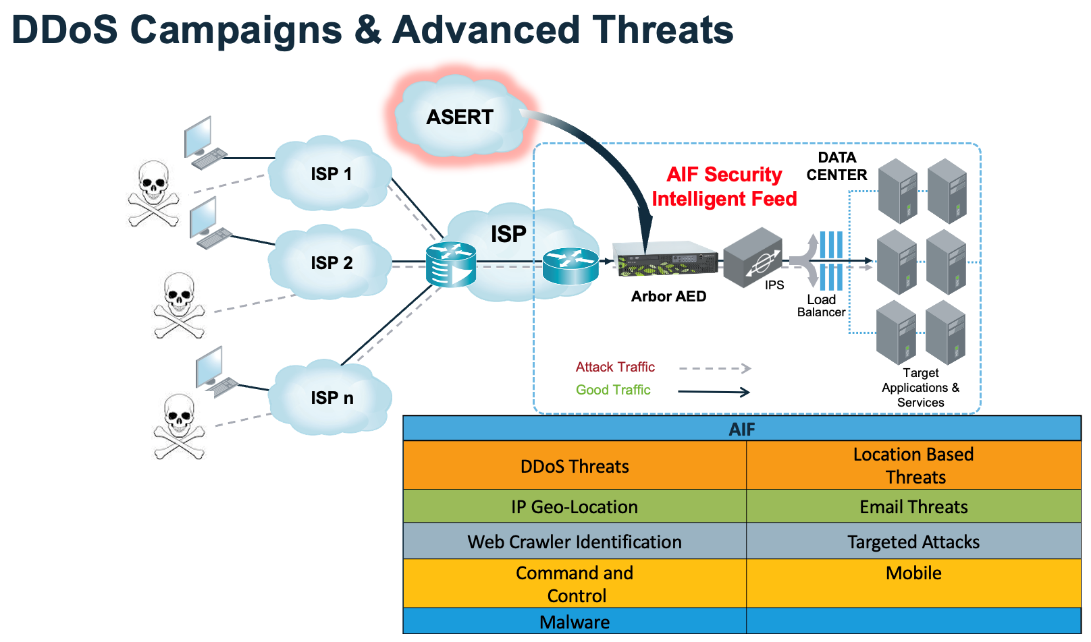
- Licensing Mechanism
The Arbor AED solution is licensed based on two main parameters:
- Clean Traffic: This refers to legitimate network traffic that is not blocked by protection policies. The Clean Traffic License defines the maximum bandwidth (in Mbps or Gbps) of legitimate traffic that the AED can process and forward. It does not include the volume of traffic that is blocked or dropped.
- AIF (ATLAS Intelligence Feed): This is the global threat intelligence data feed from NETSCOUT’s ATLAS system. The AIF license provides access to the latest threat data, including information on botnets, malicious IPs, and new DDoS attack signatures, allowing the AED to automatically update its protection policies .
- Solution Sizing Information
To properly size the solution, the following information is required:
- Current DDoS protection solutions in use.
- Specific issues the current system is facing.
- Required clean traffic license capacity (e.g., 500Mbps, 1Gbps, 2Gbps…).
- Number of internet uplink connections.
- Number and type of interfaces needed (1GE Copper/Fiber, 10GE SR/LR).
- Required duration for warranty and technical support.
- Required duration for the AIF subscription.
- Number of hardware boxes and any requirement for High Availability (HA).
- Requirement for a centralized management device.
- Technical Requirements (Reference)
The proposed solution meets the following key technical specifications:
- Protection Features: Real-time traffic monitoring with automatic detection and prevention of TCP/UDP/HTTP(S) floods, botnet attacks, anti-spoofing, and traffic shaping.
- Attack Mitigation Techniques: The system supports advanced filtering to block ICMP floods, UDP floods, and fragment floods. It can block packets based on TCP/UDP payload regular expressions. It validates DNS requests and limits query rates per second to prevent DNS-based attacks.
- Threat Intelligence: The system supports blacklisting by IP, country, domain, and URL. It uses reputation blocking based on the AIF feed. It can integrate with third-party Indicators of Compromise (IOCs) via the STIX/TAXII standard, supporting at least 3 million IOCs.
- Update Capability: The system can automatically or manually update its attack signature database from the vendor.
- Cloud Integration: The system supports “Cloud Signaling” to automatically or manually redirect traffic to an upstream cloud scrubbing service during large-scale volumetric attacks.
- Performance and Availability: The system offers low latency (< 80 microseconds) and can be upgraded via license to 40 Gbps of clean traffic without a hardware change. It supports hardware and software bypass, redundant power supplies, and RAID 1 SSDs for high availability.
We’re Ready To Help You
Get in touch with us today and let’s start transforming your business from the ground up.